Advanced Threat Protection for Modern Businesses | SNSKIES FZ LLC

Uncategorized Advanced Threat Protection for Modern Businesses | SNSKIES FZ LLC Uncategorized Advanced Threat Protection for Modern Businesses | SNSKIES FZ LLC Uncategorized April 9, 2025 In a world where digital threats evolve faster than ever, protecting sensitive data demands more than just basic firewalls and antivirus software. Organizations today need to outpace sophisticated attacks with intelligent, proactive defenses. That’s where Advanced Threat Protection (ATP) comes in — and SNSKIES FZ LLC is here to deliver. What is Advanced Threat Protection? Advanced Threat Protection is a strategic framework of security tools and techniques designed to detect, prevent, and respond to cyber threats — even those that use unknown or complex attack methods. Unlike traditional solutions that focus only on known threats, ATP delves deeper, identifying anomalies and unusual behaviors across your network. At SNSKIES FZ LLC, we implement ATP to not just protect, but anticipate — ensuring your digital assets stay a step ahead of attackers. Why ATP Matters: Key Benefits of Advanced Threat Protection Choosing a tailored ATP solution from SNSKIES FZ LLC brings crucial advantages to your organization: Real-Time Threat Visibility Gain immediate insight into malicious activity before it escalates. Shared Cloud Intelligence Leverage global intelligence feeds to stay ahead of new and evolving threats. Centralized Context and Correlation Connect threat signals across your entire infrastructure for faster decision-making. Common Tactics in Advanced Threat Attacks Understanding how attackers operate helps you defend smarter. Some of the most common strategies include: Phishing: Manipulating users into revealing confidential information. Malware Installation: Infiltrating systems with malicious code. Password Cracking: Exploiting weak or reused credentials. Backdoor Creation: Installing secret access points to bypass security. These tactics often blend into legitimate traffic, making ATP in cyber security an essential layer of defense. Essential Tools Behind ATP At SNSKIES FZ LLC, we utilize a modern stack of advanced tools to build a resilient cybersecurity environment: Next-Generation Firewalls (NGFW) Intrusion Detection & Prevention Systems (IDPS) Security Information and Event Management (SIEM) Threat Intelligence Platforms Endpoint Detection and Response (EDR) These technologies allow for real-time monitoring, incident response, and deep analytics to mitigate threats early. Monitoring and Responding with Precision Detection is just the first step. ATP requires agile and adaptive response mechanisms. Our comprehensive approach includes: Incident Response Planning – Ready-to-execute protocols for any breach scenario. Threat Hunting – Proactive search for undetected threats within systems. Security Orchestration, Automation, and Response (SOAR) – Streamlining workflows and minimizing manual errors. How Advanced Threat Protection Works SNSKIES FZ LLC implements ATP through a layered methodology that involves: Network Traffic Analysis – Monitoring unusual patterns and anomalies. Threat Intelligence Sharing – Collaborating with external intelligence sources for enhanced protection. Sandboxing – Isolating suspicious files in a safe environment to evaluate behavior before release. Step-by-Step ATP Implementation Process Ensuring maximum protection involves more than just deploying tools. Our ATP integration process includes: Define Objectives and Requirements Align ATP goals with business needs. Security Assessment Identify existing vulnerabilities and gaps. Research and Select ATP Solution Choose the best technology tailored to your industry. Pilot Testing Evaluate in a controlled environment before full rollout. Plan for Deployment Create a strategic roadmap for seamless implementation. Configure and Customize Adjust tools to align with your operations and risk profile. Integrate with Existing Tools Ensure compatibility and enhance current security infrastructure. User Training and Awareness Educate employees to recognize and report suspicious activity. Monitor and Fine-tune Continuously optimize settings based on real-time data. Continuous Improvement Adapt to new threats with regular reviews and upgrades. Secure Your Future with SNSKIES FZ LLC Cyber threats aren’t going away — they’re getting smarter. That’s why organizations turn to SNSKIES FZ LLC for Advanced Threat Protection that goes beyond the basics. With a proven methodology, intelligent tools, and a people-first approach, we ensure your digital environment is secure, agile, and future-ready. Recent Post All Posts Articles SMTP & SMTP Server Solutions | Reliable Email Infrastructure – SNSKIES FZ LLC April 8, 2025/ Firewall vs. IDS vs. IPS: Understanding the Key Differences in Network Security March 27, 2025/ Snskies FZ LLC Cloud Security Services: Cloud Security Posture Assessments & DevSecOps March 25, 2025/ Older Posts
SMTP & SMTP Server Solutions | Reliable Email Infrastructure – SNSKIES FZ LLC
Uncategorized SMTP & SMTP Server Solutions | Reliable Email Infrastructure – SNSKIES FZ LLC Uncategorized SMTP & SMTP Server Solutions | Reliable Email Infrastructure – SNSKIES FZ LLC Uncategorized April 8, 2025 In the realm of digital communication, email remains a cornerstone for both personal and professional interaction. The driving force behind email delivery is SMTP—Simple Mail Transfer Protocol. At SNSKIES FZ LLC, we provide enterprise-level SMTP server solutions designed to ensure secure, scalable, and high-performance email delivery for businesses worldwide. What is SMTP? SMTP (Simple Mail Transfer Protocol) is a standard communication protocol used for sending and relaying email messages over the internet. It enables email servers and applications to communicate, ensuring that messages are delivered from one server to another accurately and efficiently. Whether sending transactional emails, alerts, or large-scale email campaigns, SMTP is the foundational protocol that makes it possible. How Does SMTP Work? The SMTP process involves a structured series of steps that ensure message delivery: Connection Initiation: The email client establishes a connection with the SMTP server. Data Transmission: Sender details, recipient address, and message content are submitted to the server. Message Relay: The message is transferred from one server to the next until it reaches the destination server. Connection Termination: The communication session is closed after successful transmission. SMTP: A Breakdown of the Protocol S – Simple: Easy to implement, configure, and maintain. M – Mail: Specifically developed for electronic mail services. T – Transfer: Transfers messages reliably across multiple networks. P – Protocol: A standardized set of rules for email transmission between servers. What is an SMTP Server? An SMTP server is the backbone of outgoing email. It acts as an intermediary that receives emails from clients and forwards them to the intended recipient’s server. It uses the SMTP protocol to handle authentication, routing, and delivery. At SNSKIES FZ LLC, we offer custom SMTP server solutions that support high-volume sending, robust authentication, and real-time monitoring. What is an SMTP Email Service? An SMTP email service is a managed platform that handles all aspects of email delivery infrastructure on your behalf. Key features include: Improved Deliverability: Helps ensure emails reach inboxes. Built-in Security: Enforces protocols like SPF, DKIM, and DMARC to protect against spoofing and spam. Analytics & Reporting: Offers insights on email performance metrics such as delivery rates, bounces, and engagement. With SNSKIES FZ LLC, clients gain access to a fully managed SMTP infrastructure that scales with business needs while ensuring compliance and performance. The Role of SMTP in Email Delivery The email delivery workflow through SMTP includes: The client establishes a connection with the SMTP server. Authentication is performed to verify the sender’s identity. The server accepts and processes the message content. The recipient server validates DNS records and security checks. If approved, the message is stored for retrieval via POP3 or IMAP. Key Mail Agents in SMTP Architecture Understanding the different mail agents involved helps clarify the overall SMTP process: MUA (Mail User Agent): The email application used by the sender. MSA (Mail Submission Agent): Accepts the message from the MUA. MTA (Mail Transfer Agent): Transfers the message across networks. MDA (Mail Delivery Agent): Delivers the message to the recipient’s mailbox. Why Choose SNSKIES FZ LLC? When it comes to SMTP and SMTP server solutions, SNSKIES FZ LLC stands out by offering: Fully managed, high-availability SMTP servers Scalable email delivery solutions for all industries Compliance with global standards and security protocols 24/7 monitoring, analytics, and technical support Recent Post All Posts Articles Firewall vs. IDS vs. IPS: Understanding the Key Differences in Network Security March 27, 2025/ Snskies FZ LLC Cloud Security Services: Cloud Security Posture Assessments & DevSecOps March 25, 2025/ SASE & Zero Trust Implementation by snskies fz llc March 21, 2025/ Older Posts
Firewall vs. IDS vs. IPS: Understanding the Key Differences in Network Security
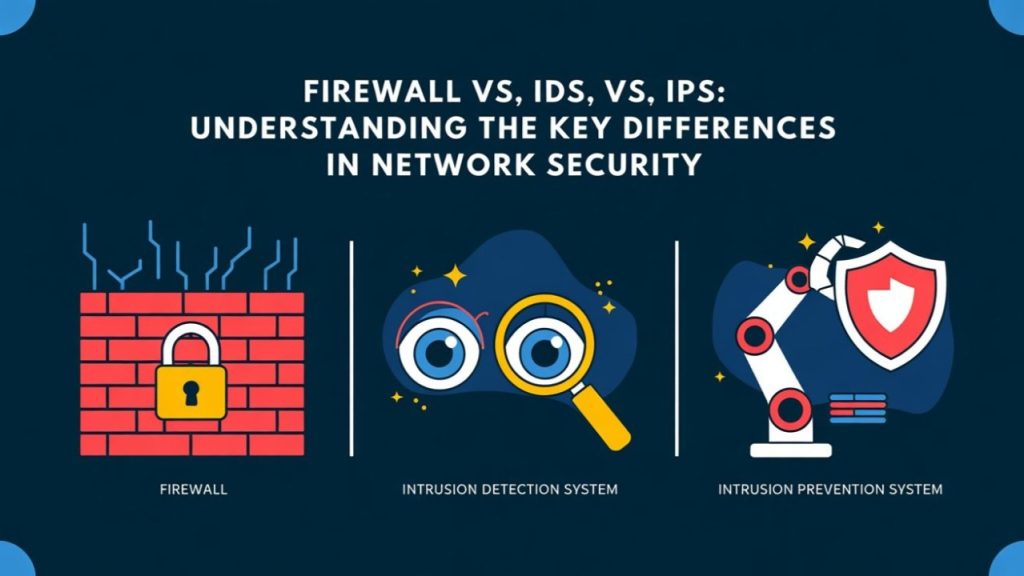
Articles Penetration Testing & Red Teaming by snskies fz llc Articles Penetration Testing & Red Teaming by snskies fz llc Articles March 20, 2025 In today’s interconnected world, securing your network is no longer optional—it’s a necessity. Three common solutions that often come up in discussions of cybersecurity are firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS). Although they may sound similar, each plays a distinct role in protecting your network. In this article, we will explore the differences between these technologies, their key features, and how to choose the best option for your organization. Table of Contents What Is a Firewall? What Is an Intrusion Detection System (IDS)? What Is an Intrusion Prevention System (IPS)? Key Differences Among Firewall, IDS, and IPS Benefits and Use Cases Choosing the Right Solution Conclusion Frequently Asked Questions (FAQs) What Is a Firewall? A firewall is often considered the first line of defense in network security. It monitors and controls incoming and outgoing network traffic based on predefined security rules. Firewalls can be hardware devices, software applications, or a combination of both. Key Features of a Firewall Packet Filtering: Examines packets of data to allow or block them based on IP addresses, protocols, and ports. Stateful Inspection: Tracks the state of active connections to make filtering decisions more intelligent. Proxy Service: Acts as an intermediary for requests from clients seeking resources from other servers, adding an extra layer of protection. Application-Level Filtering: Analyzes data from specific applications (e.g., HTTP, FTP) to detect malicious activity. What Is an Intrusion Detection System (IDS)? An Intrusion Detection System (IDS) is designed to detect suspicious activities or policy violations within a network or host system. Unlike firewalls, IDS solutions typically do not block traffic; instead, they alert administrators about potential intrusions so that manual or automated responses can be initiated. Types of IDS Network-Based IDS (NIDS): Monitors traffic across an entire network. Host-Based IDS (HIDS): Monitors traffic or system logs on a single host, analyzing user and system activities. How IDS Works Signature-Based Detection: Uses known attack patterns (signatures) to identify threats. Anomaly-Based Detection: Establishes a baseline of normal activity and flags deviations as potential threats. What Is an Intrusion Prevention System (IPS)? An Intrusion Prevention System (IPS) takes the functionality of an IDS a step further by not only detecting malicious activities but also blocking or preventing them in real time. Think of it as an IDS with active response capabilities. How IPS Works Real-Time Monitoring: Continuously scans network traffic for suspicious patterns. Automated Response: Blocks or quarantines malicious traffic based on predefined rules or anomaly detection. Integration with Other Security Tools: Often integrated with firewalls or security management systems to provide a coordinated defense. Key Differences Among Firewall, IDS, and IPS Benefits and Use Cases Benefits of Firewalls Simple and Effective: Ideal for basic traffic filtering. Low Overhead: Generally less resource-intensive. Broad Coverage: Protects against a wide range of external threats. Benefits of IDS Detailed Monitoring: Provides insights into network and system behavior. High Visibility: Offers comprehensive logs for forensic analysis. Adaptability: Can be configured to detect new or unknown threats using anomaly-based detection. Benefits of IPS Proactive Security: Automatically stops attacks in real time. Reduced Manual Intervention: Frees up security teams by blocking threats automatically. Integrated Defense: Works well alongside other security tools for a layered security approach. Choosing the Right Solution Assess Your Risk Level: Organizations with critical data and stringent compliance requirements may need an IPS for real-time blocking, while smaller businesses might start with a robust firewall and IDS combination. Consider Resources: An IPS typically requires more advanced configuration and monitoring. Ensure your team has the expertise to manage it. Layered Security Approach: No single solution is a silver bullet. A combination of firewall, IDS, and IPS often yields the best protection. Conclusion A robust security posture involves understanding the differences and synergies between firewalls, IDS, and IPS. While firewalls offer a foundational barrier, IDS provides deep visibility, and IPS delivers automated, proactive threat mitigation. Most organizations benefit from deploying all three in a layered security model to ensure comprehensive protection. Frequently Asked Questions (FAQs) Can I replace my firewall with an IDS or IPS? No. Firewalls and IDS/IPS serve different but complementary roles. Firewalls block unauthorized traffic at the perimeter, whereas IDS/IPS focus on detecting and responding to threats inside the network. Do I need both IDS and IPS? Many modern security appliances combine IDS and IPS functionalities. However, in high-security environments, separate systems may be used for specialized monitoring and more granular control. Which is more important: firewall, IDS, or IPS? All are important in a layered security strategy. A firewall provides the first layer of defense, an IDS adds visibility and detection, and an IPS offers proactive prevention. Is an IPS always better than an IDS? Not necessarily. An IPS offers automated blocking, but an IDS can be more cost-effective and simpler to manage, especially for smaller organizations or those with limited security expertise. How do I choose the right security vendor? Look for reputable vendors with a proven track record, robust customer support, and solutions that can integrate with your existing infrastructure. Recent Post All Posts Articles Snskies FZ LLC Cloud Security Services: Cloud Security Posture Assessments & DevSecOps March 25, 2025/ SASE & Zero Trust Implementation by snskies fz llc March 21, 2025/ Penetration Testing & Red Teaming by snskies fz llc March 20, 2025/ Older Posts
Snskies FZ LLC Cloud Security Services: Cloud Security Posture Assessments & DevSecOps

Articles Leading Forensics & Incident Response (DFIR) Services by snskies fz llc Articles Leading Forensics & Incident Response (DFIR) Services by snskies fz llc Articles March 19, 2025 At Snskies FZ LLC, we specialize in delivering top-tier cloud security solutions that empower businesses to operate securely in an increasingly digital world. With a strong focus on cybersecurity, compliance, and risk management, our mission is to help organizations protect their cloud infrastructure, mitigate potential threats, and ensure seamless business operations. Our expert team leverages the latest security technologies and best practices to safeguard data, applications, and networks against evolving cyber threats. Why Choose Snskies FZ LLC for Cloud Security? In the ever-evolving digital landscape, businesses require robust cloud security solutions to safeguard their data and operations. Snskies FZ LLC is a leading provider of comprehensive cloud security services, ensuring that organizations can operate with confidence in the cloud. Our expertise in cybersecurity, compliance, and risk management helps businesses mitigate threats and enhance their cloud security posture. Cloud Security and the Shared Responsibility Model Cloud security operates under a shared responsibility model, where both the cloud provider and the customer have defined security obligations: Cloud Provider Responsibilities: Securing the cloud infrastructure, including physical security, network protection, and platform patching. Customer Responsibilities: Managing access controls, securing data, and ensuring proper application configurations. Key Challenges in Cloud Security Organizations face several challenges in maintaining cloud security, including: Expanded Attack Surface: More entry points for cyber threats due to increased cloud adoption. Limited Visibility: Difficulty in tracking cloud activity and detecting anomalies. Dynamic Workloads: Continuous security updates required for changing cloud environments. DevSecOps & Automation: Integrating security seamlessly into development pipelines. Access Control & Encryption: Effective privilege management and key security. Complex Cloud Architectures: Hybrid and multi-cloud environments increase security complexity. Regulatory Compliance: Ensuring adherence to industry security standards and governance policies. Types of Cloud Environments Public Cloud: Third-party cloud services from providers like AWS, Azure, and Google Cloud. Private Cloud: Exclusive cloud infrastructure for a single organization. Hybrid Cloud: Combination of public and private clouds for security and scalability. Multi-Cloud: Leveraging multiple cloud providers to reduce risk and increase flexibility. Common Cloud Security Risks Insider Threats: Human errors, misconfigurations, and malicious insider activity. Cyberattacks: Malware infections, phishing, and data breaches. Compliance Failures: Non-adherence to regulatory and industry-specific security standards. Importance of Cloud Security A robust cloud security strategy helps: Prevent unauthorized data access. Protect sensitive business and customer information. Ensure business continuity and disaster recovery. Maintain compliance with industry regulations. Benefits of Cloud Security Cost Savings: Eliminates the need for extensive on-premises security infrastructure. Lower Operational Overheads: Automated security updates and threat management. High Availability: Reliable security measures from cloud providers. Centralized Security Management: Unified security controls and monitoring. Scalability: Adaptable security solutions for growing businesses. DDoS Protection: Robust defenses against distributed denial-of-service (DDoS) attacks. Cloud Security for Various Deployment Models Public Cloud Security Challenges: Shared infrastructure increases risks of data breaches and misconfigurations. Best Practices: Implement Identity and Access Management (IAM), encrypt sensitive data, and use Cloud Security Posture Management (CSPM) tools. Private Cloud Security Challenges: Managing internal security and ensuring regulatory compliance. Best Practices: Strong authentication protocols, periodic security audits, and intrusion detection systems. Hybrid Cloud Security Challenges: Ensuring security across different cloud environments. Best Practices: Implement unified security policies, encrypt data, and establish secure API connections. Multi-Cloud Security Challenges: Security inconsistencies across multiple cloud providers. Best Practices: Conduct Cloud Security Posture Assessments (CSPA), establish centralized monitoring, and ensure compliance across platforms. The Role of Cloud Security Posture Assessments (CSPA) Cloud Security Posture Assessments help businesses identify vulnerabilities, misconfigurations, and compliance gaps in their cloud environments. Regular assessments improve security by providing: Comprehensive Visibility: Full insight into cloud assets and configurations. Automated Compliance Checks: Streamlined adherence to industry regulations. Effective Risk Mitigation: Proactive identification and resolution of security threats. DevSecOps: Securing Development Pipelines DevSecOps integrates security into DevOps workflows to ensure robust protection throughout the software development lifecycle. Key strategies include: Security as Code: Automating security policies within CI/CD pipelines. Continuous Monitoring: Real-time detection and response to vulnerabilities. Threat Modeling: Proactively addressing potential security threats. For businesses looking to enhance cloud security, Snskies FZ LLC provides comprehensive Cloud Security Posture Assessments and DevSecOps solutions, ensuring a secure and compliant cloud infrastructure. Recent Post All Posts Articles SASE & Zero Trust Implementation by snskies fz llc March 21, 2025/ Penetration Testing & Red Teaming by snskies fz llc March 20, 2025/ Leading Forensics & Incident Response (DFIR) Services by snskies fz llc March 19, 2025/ Older Posts
SASE & Zero Trust Implementation by snskies fz llc

Articles Comprehensive Network Security Management by Snskies FZ LLC Articles Comprehensive Network Security Management by Snskies FZ LLC Articles March 18, 2025 Introduction: The Future of Secure Networking As organizations shift to remote and hybrid work environments, securing digital assets has never been more critical. snskies fz llc leads the way with advanced SASE (Secure Access Service Edge) and Zero Trust Implementation services. Our approach redefines network security by seamlessly integrating cloud-delivered security with a Zero Trust model, ensuring that every user, device, and application is continuously verified before granting access. Understanding SASE and Zero Trust Networking What is SASE? SASE converges networking and security into a single cloud-based service model. By leveraging SASE, businesses benefit from: Cloud-Delivered Security: Unified threat protection, data loss prevention, and secure web gateways. Flexible Access: Optimized connectivity for remote and mobile workforces. Scalability: Rapid deployment and seamless integration with existing cloud environments. What is Zero Trust Networking? Zero Trust is a security model that operates on the principle of “never trust, always verify.” This approach mandates that: Verification is Continuous: Every request is authenticated, authorized, and encrypted. Access is Minimal: Users are granted only the access necessary to perform their roles. Security is Proactive: Continuous monitoring and real-time analytics are used to detect and mitigate threats. The Benefits of SASE & Zero Trust Implementation Secure Remote Workforce With a growing number of employees working remotely, traditional perimeter-based security is no longer sufficient. SASE ensures that: Every Connection is Secure: Encrypted tunnels and identity-based policies protect remote sessions. Consistent Security Policies: Uniform security controls are enforced regardless of location. Improved User Experience: Optimized network performance with reduced latency and faster access to applications. Enhanced Network Security with Zero Trust Implementing Zero Trust transforms your network by: Eliminating Implicit Trust: No user or device is trusted by default, reducing the risk of insider threats. Real-Time Threat Detection: Continuous validation and monitoring help identify anomalies and potential breaches. Granular Access Control: Detailed access policies ensure that sensitive data is accessible only to authorized users. snskies fz llc’s Approach to SASE & Zero Trust Strategic Assessment & Planning Our team begins with an in-depth assessment of your current network architecture and security posture. We identify vulnerabilities and design a customized roadmap for SASE and Zero Trust implementation that aligns with your business objectives. Seamless Integration & Deployment We deploy our solutions with minimal disruption, ensuring: Smooth Transition: Integration with existing infrastructure and cloud services. Scalable Solutions: Our services grow with your business, adapting to evolving threats. End-to-End Security: Comprehensive protection across all network layers, from the cloud to endpoints. Continuous Monitoring & Optimization Security is an ongoing journey. We provide: Real-Time Analytics: Continuous monitoring to detect and respond to threats instantly. Regular Audits: Frequent assessments to ensure compliance with the latest security standards. Adaptive Security Policies: Dynamic policies that evolve based on new threats and business needs. Why Choose snskies fz llc? Expertise: Our team of cybersecurity professionals is dedicated to staying ahead of emerging threats. Tailored Solutions: We design and implement security measures specific to your organization’s needs. Proven Track Record: Trusted by numerous businesses, we consistently deliver robust, scalable, and effective security solutions. Innovation: We combine the best of SASE and Zero Trust to provide a future-proof security framework for your business. Secure Your Future Today In today’s digital age, a proactive security strategy is essential. snskies fz llc empowers your organization with SASE and Zero Trust Implementation to safeguard your remote workforce and secure your network. Contact us today to transform your security infrastructure and build a resilient digital environment. Recent Post All Posts Articles Penetration Testing & Red Teaming by snskies fz llc March 20, 2025/ Leading Forensics & Incident Response (DFIR) Services by snskies fz llc March 19, 2025/ Comprehensive Network Security Management by Snskies FZ LLC March 18, 2025/ Older Posts
Penetration Testing & Red Teaming by snskies fz llc

Articles DNS Security | Protecting Your Business from Cyber Threats Articles DNS Security | Protecting Your Business from Cyber Threats Articles March 14, 2025 Introduction: Elevating Your Cybersecurity Strategy As cyber threats evolve in complexity, organizations need proactive measures to protect critical assets and data. snskies fz llc specializes in Penetration Testing & Red Teaming—two powerful approaches that go beyond traditional security checks to uncover hidden weaknesses and enhance your overall cybersecurity posture. By leveraging vulnerability assessments and ethical hacking, we help businesses identify, prioritize, and remediate risks before they become serious incidents. What Are Penetration Testing & Red Teaming? Penetration Testing Penetration Testing is a methodical process of simulating cyberattacks on your organization’s systems, networks, and applications. Skilled ethical hackers use real-world tactics to: Identify security gaps and misconfigurations Exploit vulnerabilities to gauge potential impact Provide actionable recommendations to strengthen defenses Red Teaming Red Teaming is a more holistic, full-scope approach that involves emulating advanced threat actors to test not just technical defenses but also the organization’s people, processes, and physical security. The Red Team actively attempts to breach your security using stealth and creativity, while a Blue Team (your internal security or IT staff) works to detect and respond. This exercise provides critical insights into: Incident response readiness Detection and monitoring capabilities Internal communication and escalation procedures By combining penetration testing and red teaming, organizations gain a robust view of their security posture, ensuring any blind spots are quickly identified and addressed. Why Vulnerability Assessments & Ethical Hacking Matter 1. Proactive Threat Identification Relying solely on firewalls and antivirus solutions is insufficient. Regular vulnerability assessments ensure you remain ahead of emerging threats, while ethical hacking techniques simulate real attacks to reveal the true extent of your defenses. 2. Risk Prioritization Not all vulnerabilities pose the same level of risk. Our assessments rank potential threats based on severity, enabling you to allocate resources effectively and tackle the most critical issues first. 3. Compliance & Regulatory Requirements Many industries are governed by strict data protection regulations (e.g., GDPR, HIPAA, PCI-DSS). Comprehensive penetration testing helps demonstrate due diligence, minimizing legal and financial repercussions. 4. Protect Reputation & Customer Trust Data breaches can damage brand reputation and erode customer confidence. Proactively strengthening security through red teaming and penetration testing safeguards your organization’s image and instills trust in stakeholders. snskies fz llc’s Approach to Penetration Testing & Red Teaming Phase 1: Planning & Scoping Our experts collaborate with your team to define objectives, clarify the scope, and understand your environment’s specific threats. This ensures that tests accurately reflect potential real-world scenarios. Phase 2: Reconnaissance & Vulnerability Discovery We conduct thorough reconnaissance—gathering intelligence on your infrastructure, applications, and network. Advanced tools and manual techniques are used to uncover: Software flaws and outdated systems Misconfigured devices Weak credentials and default passwords Phase 3: Exploitation & Lateral Movement Leveraging the identified vulnerabilities, our ethical hackers attempt to exploit entry points to: Gain unauthorized access Escalate privileges Move laterally across your network During this phase, we meticulously document each step to help you understand the severity and impact of discovered vulnerabilities. Phase 4: Reporting & Recommendations We compile a comprehensive report detailing our findings, including: Technical breakdown of exploited vulnerabilities Visual proof of concept where applicable Prioritized remediation steps Our team then collaborates with your security or IT department to ensure effective resolution of identified issues. Phase 5: Retesting & Ongoing Security Security is not a one-time event. After implementing the recommended fixes, snskies fz llc offers retesting services to confirm that vulnerabilities have been effectively addressed. Additionally, we can provide continuous monitoring and advisory services to maintain a strong security posture. Why Choose snskies fz llc for Ethical Hacking & Red Teaming Certified Experts: Our team comprises OSCP, CEH, and CISSP-certified professionals with deep expertise in ethical hacking and cyber defense. Tailored Methodology: We design each engagement to address your specific environment, business goals, and regulatory requirements. Proven Tools & Techniques: Using industry-leading platforms and proprietary tools, we accurately simulate sophisticated attacks to deliver realistic results. Comprehensive Reporting: Our clear, actionable reports facilitate swift remediation and better communication between technical and non-technical stakeholders. Client-Centric Focus: We value collaboration, ensuring you stay informed and empowered throughout the testing process. Protect Your Organization with snskies fz llc Cyber threats can strike at any time. By proactively identifying and remediating weaknesses through Penetration Testing & Red Teaming, you can fortify your defenses and maintain trust with your customers and partners. Contact snskies fz llc today to learn how our vulnerability assessments and ethical hacking services can enhance your cybersecurity posture. With our expertise and client-focused approach, we help you stay a step ahead of evolving threats—safeguarding your critical data and business continuity. Recent Post All Posts Articles Leading Forensics & Incident Response (DFIR) Services by snskies fz llc March 19, 2025/ Comprehensive Network Security Management by Snskies FZ LLC March 18, 2025/ DNS Security | Protecting Your Business from Cyber Threats March 14, 2025/ Older Posts
Leading Forensics & Incident Response (DFIR) Services by snskies fz llc

Articles Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE Articles Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE Articles March 13, 2025 Introduction: Securing Your Digital Future In today’s fast-paced digital landscape, cyber threats are becoming more sophisticated and persistent. Businesses need robust strategies to detect, respond to, and mitigate security incidents. At snskies fz llc, we provide comprehensive DFIR solutions designed to protect your assets, maintain operational integrity, and secure your reputation. Our specialized approach in breach investigation and forensic analysis ensures rapid response and actionable insights. What is DFIR and Why It Matters Understanding DFIR Digital Forensics and Incident Response (DFIR) is the backbone of modern cybersecurity. It involves: Digital Forensics: The scientific process of collecting, preserving, and analyzing digital evidence. Incident Response: A structured approach to managing and mitigating security breaches as they occur. This dual approach enables organizations to not only understand how a breach happened but also to remediate vulnerabilities swiftly. The Growing Need for DFIR With the surge in cyberattacks—ransomware, data breaches, and advanced persistent threats—DFIR has become indispensable. Companies face severe consequences from breaches, including financial losses, reputational damage, and regulatory penalties. Implementing a robust DFIR strategy is no longer optional; it’s a critical investment in your company’s future. Comprehensive Forensics Lab at snskies fz llc At the heart of our DFIR operations is our advanced Forensics Lab, a central hub equipped with specialized facilities for every stage of digital investigation. This integrated approach ensures every piece of evidence is meticulously handled and analyzed. The Forensics Lab includes the following specialized areas: Darknet Lab Investigates hidden or anonymized channels to gather actionable intelligence on threat actors, illicit activities, and potential vulnerabilities. Network Forensics Monitors and analyzes network traffic to detect anomalies, trace attack vectors, and gather digital evidence critical for incident response. Computer Forensics Focuses on the extraction, preservation, and examination of data from computer systems, ensuring no evidence is overlooked. Mobile Forensics Specializes in retrieving and analyzing data from smartphones and other mobile devices, critical in modern breach investigations. Advanced Recovery Lab Employs cutting-edge tools to restore data from corrupted, encrypted, or physically damaged storage devices. OSINT & Social Media Leverages open-source intelligence to track cyber threats, malicious campaigns, and brand reputation risks across social platforms. Lab On Wheels Enables on-site forensics and incident response, bringing advanced investigative capabilities directly to your location. Audio/Video Forensics Extracts and enhances relevant evidence from audio recordings, CCTV footage, and other media sources. Password Recovery Lab Utilizes specialized techniques and software to crack or reset passwords, essential in uncovering hidden or encrypted data. On-Scene Forensics Conducts meticulous digital investigations at the physical site of an incident, preserving the chain of custody. Cyber Intelligence Solutions Delivers real-time threat intelligence, helping organizations anticipate, detect, and neutralize emerging cyber threats. Customised Tools Develops tailored solutions and scripts to handle unique investigative challenges and complex digital environments. Central Lab Serves as the coordinating nucleus for all forensic processes, ensuring seamless collaboration across each specialized sub-lab. Our Approach to Breach Investigation Rapid Breach Identification When a breach is detected, every minute counts. Our team at snskies fz llc quickly isolates affected systems and deploys state-of-the-art tools to identify the attack vector. This proactive approach minimizes downtime and limits potential damage. Comprehensive Forensic Analysis We conduct thorough forensic investigations to: Collect Digital Evidence: Securely retrieve data from affected systems while preserving its integrity. Analyze Attack Patterns: Leverage advanced analytics to reconstruct the breach and understand the attacker’s methodology. Provide Actionable Insights: Deliver clear, concise reports that help you enhance your security posture and prevent future incidents. Case Studies and Success Stories Our proven track record includes numerous successful breach investigations where our forensic analysis has: Uncovered hidden malware and root causes. Aided in legal proceedings and regulatory compliance. Informed strategic investments in cybersecurity improvements. Incident Response Process: How We Protect Your Business 1. Preparation and Planning We work closely with your organization to establish a robust incident response plan. Our experts conduct risk assessments and simulate breach scenarios to ensure that your team is ready when every second matters. 2. Detection and Analysis Utilizing cutting-edge monitoring tools, we continuously watch for suspicious activities. When an incident is detected, our team immediately initiates the analysis process to confirm and evaluate the threat. 3. Containment, Eradication, and Recovery Our structured response includes: Containment: Isolating affected networks to prevent further spread. Eradication: Removing malicious components from your systems. Recovery: Restoring systems to normal operations while reinforcing security measures. 4. Post-Incident Review After resolving an incident, we conduct a comprehensive review to extract lessons learned and refine your security protocols. This feedback loop is critical for evolving your defense strategies in an ever-changing threat landscape. Why Choose snskies fz llc for Your DFIR Needs? Expert Team: Our specialists are certified professionals with extensive experience in cybersecurity, digital forensics, and incident management. Advanced Tools & Techniques: We use the latest technology to ensure that our forensic analysis is both thorough and reliable. Tailored Solutions: Every business is unique. We customize our DFIR strategies to meet your specific needs and regulatory requirements. Proven Track Record: With successful breach investigations across multiple industries, our expertise speaks for itself. All-Inclusive Forensics Lab: Our specialized labs—from Darknet analysis to on-site forensics—cover every aspect of digital investigation, ensuring no stone is left unturned. Protect Your Business Today Cybersecurity is an ongoing battle. Don’t wait until a breach compromises your business integrity. Contact snskies fz llc today to learn how our DFIR services can fortify your defenses, provide rapid incident response, and guide you through comprehensive forensic analysis. Secure your future with a partner you can trust. Recent Post All Posts Articles Comprehensive Network Security Management by Snskies FZ LLC March 18, 2025/ DNS Security | Protecting Your Business from Cyber Threats March 14, 2025/ Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE March 13, 2025/ Older Posts
Comprehensive Network Security Management by Snskies FZ LLC
Articles Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE Articles Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE Articles March 13, 2025 In today’s ever-evolving digital landscape, businesses need robust network security to protect their data and operations. Snskies FZ LLC delivers top-tier Network Security Management solutions, specializing in advanced firewalls, cutting-edge IDS/IPS, secure VPN configurations, and innovative SD-WAN security. This article explores how our comprehensive services fortify your network against cyber threats and ensure seamless connectivity. The Importance of Network Security Management Effective network security management is critical for every organization. Cyber threats such as malware, phishing attacks, and data breaches are constantly evolving, making it essential to deploy a multi-layered defense strategy. Snskies FZ LLC’s solutions not only protect your digital assets but also ensure compliance with industry standards and regulations. Key benefits include: Risk Reduction: Minimize vulnerabilities with proactive security measures. Business Continuity: Ensure uninterrupted operations with resilient systems. Data Protection: Safeguard sensitive information from unauthorized access. Regulatory Compliance: Meet and exceed industry standards for data security. Advanced Firewall Solutions Why Firewalls Matter Firewalls serve as the first line of defense in network security by monitoring and controlling incoming and outgoing traffic based on predetermined security rules. They block malicious traffic and prevent unauthorized access, ensuring that only trusted data passes through your network. Snskies FZ LLC’s Firewall Capabilities At Snskies FZ LLC, our firewall solutions are designed to: Detect and Block Threats: Advanced algorithms identify potential threats in real time. Customizable Security Policies: Tailor your firewall settings to match your organization’s unique requirements. Scalable Protection: Adapt to the changing needs of your network as your business grows. IDS/IPS: Intelligent Detection and Prevention Understanding IDS and IPS Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are critical components of a comprehensive security strategy. IDS monitors network traffic for suspicious activities, while IPS takes action to block or mitigate identified threats in real time. How Snskies FZ LLC Enhances IDS/IPS Our approach includes: Real-Time Monitoring: Constantly scanning your network to detect unusual patterns and potential breaches. Automated Response: Rapidly isolating threats before they can compromise your network. Detailed Analytics: Providing in-depth reports to help you understand and respond to security incidents. VPN Security: Secure Remote Access The Role of VPNs in Modern Business A Virtual Private Network (VPN) creates a secure connection over the internet, allowing remote users to access your network safely. VPNs encrypt data in transit, ensuring that sensitive information remains confidential even when accessed from remote locations. Snskies FZ LLC’s VPN Solutions Our VPN security offerings are designed to: Encrypt Data: Utilize robust encryption protocols to protect data integrity. Enhance Mobility: Enable secure access for remote employees, facilitating flexible work environments. Maintain Confidentiality: Ensure that all communications remain private and secure from eavesdropping. SD-WAN Security: Modernizing Network Infrastructure What is SD-WAN? Software-Defined Wide Area Network (SD-WAN) technology optimizes connectivity across geographically dispersed locations. It offers dynamic, cost-effective management of network traffic while integrating robust security features. Securing Your SD-WAN with Snskies FZ LLC Our SD-WAN security services include: Centralized Management: Streamline network control through a unified platform. Integrated Security: Combine firewall, IDS/IPS, and VPN functionalities for comprehensive protection. Enhanced Performance: Optimize bandwidth usage while maintaining high levels of security across all endpoints. Why Choose Snskies FZ LLC? Snskies FZ LLC stands out as a leader in network security management by offering a full spectrum of services designed to safeguard your business. Our commitment to cutting-edge technology and proactive security measures means you benefit from: Expert Guidance: Our team of cybersecurity professionals is dedicated to crafting solutions that meet your unique needs. Tailored Solutions: We understand that each organization has distinct requirements; our services are customized to fit your business model. Reliable Support: Enjoy round-the-clock monitoring and expert support to keep your network secure. Conclusion In a world where cyber threats are becoming increasingly sophisticated, robust network security is non-negotiable. Snskies FZ LLC’s comprehensive approach—combining advanced firewalls, intelligent IDS/IPS, secure VPN configurations, and innovative SD-WAN security—ensures your network remains protected and resilient. Invest in a future-proof security infrastructure with Snskies FZ LLC and experience the peace of mind that comes with complete network protection. Recent Post All Posts Articles Comprehensive Network Security Management by Snskies FZ LLC March 18, 2025/ DNS Security | Protecting Your Business from Cyber Threats March 14, 2025/ Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE March 13, 2025/ Older Posts
DNS Security | Protecting Your Business from Cyber Threats

Articles Fortinet Achieves Prestigious Recognition for Zero Trust Network Access (ZTNA) Articles Fortinet Achieves Prestigious Recognition for Zero Trust Network Access (ZTNA) Articles March 6, 2025 What Is DNS Security? The Domain Name System (DNS) acts as the internet’s directory, translating user-friendly domain names (e.g., example.com) into numerical IP addresses. DNS security encompasses the protocols, tools, and practices designed to protect this critical system from cyberattacks. By securing DNS infrastructure, organizations ensure uninterrupted connectivity, prevent data breaches, and maintain user trust. How Does DNS Work? DNS operates through a hierarchical network of servers: Recursive Resolver: Handles user queries and communicates with other DNS servers. Root Server: Directs resolvers to Top-Level Domain (TLD) servers (e.g., .com, .net). Authoritative Server: Provides the final IP address linked to the requested domain.While this process is efficient, its decentralized nature makes it vulnerable to exploitation Why Is DNS Security Critical for Businesses? Prevents Malicious Redirection: Blocks access to phishing or fraudulent websites. Mitigates Downtime: Protects against attacks like DDoS that disrupt services. Stops Data Exfiltration: Detects and blocks DNS tunneling used to leak sensitive data. Ensures Compliance: Helps meet regulations like GDPR by safeguarding user privacy. A compromised DNS can lead to financial losses, legal repercussions, and reputational harm. 4 Common DNS Attacks and Mitigation Strategies 1. DoS/DDoS and DNS Amplification Attack Method: Overwhelms servers with fake requests or exploits open resolvers to amplify traffic. Prevention: Use traffic filtering, rate limiting, and deploy Anycast DNS for load distribution. 2. DNS Spoofing (Cache Poisoning) Attack Method: Injects false DNS records to redirect users to malicious sites. Prevention: Implement DNSSEC to authenticate DNS responses. 3. DNS Tunneling Attack Method: Uses DNS queries to bypass security controls and exfiltrate data. Prevention: Monitor DNS traffic for anomalies and block suspicious domains. 4. DNS Hijacking Attack Method: Alters DNS settings to redirect traffic to attacker-controlled servers. Prevention: Secure DNS management interfaces with multi-factor authentication (MFA). Core DNS Security Solutions 1. DNSSEC (DNS Security Extensions) Adds cryptographic signatures to DNS records to verify authenticity and prevent tampering. 2. DNS Filtering Leverages threat intelligence to block access to malicious or high-risk domains. 3. Advanced Firewalls Inspect and filter DNS traffic to detect anomalies and enforce security policies. 4. Redundant DNS Architecture Deploy primary and secondary servers to ensure high availability during attacks. DNS Security Best Practices Enable Detailed Logging: Track DNS queries to identify unusual patterns. Secure DNS Caches: Restrict write-access to prevent cache poisoning. Filter DNS Traffic: Block requests to known malicious domains. Enforce Access Controls: Limit administrative privileges to DNS servers. Adopt Zero Trust Principles: Validate all DNS requests, including internal traffic. DNS, DNSSEC, and DNS Security: Key Differences DNS: The foundational system that maps domains to IP addresses. DNSSEC: A protocol extension that adds cryptographic authentication to DNS data. DNS Security: A comprehensive approach combining DNSSEC, monitoring, and threat prevention. Emerging DNS Security Trends in 2024 Healthcare Sector Focus: Protecting IoT medical devices and patient data portals. Hybrid Work Challenges: Securing DNS in multi-cloud and remote work environments. IoT Whitelisting: Restricting DNS access for connected devices to minimize risks. AI-Powered Analytics: Automating threat detection through DNS traffic analysis. Conclusion DNS security is vital for maintaining a secure and resilient network. By addressing threats like DDoS, spoofing, and hijacking through solutions such as DNSSEC, traffic filtering, and redundant architectures, businesses can safeguard their digital operations. Adopting best practices like logging, access controls, and Zero Trust principles ensures long-term protection against evolving cyber threats. Prioritizing DNS security is not just a technical necessity—it’s a cornerstone of modern cybersecurity strategy. Recent Post All Posts Articles DNS Security | Protecting Your Business from Cyber Threats March 14, 2025/ Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE March 13, 2025/ Fortinet Achieves Prestigious Recognition for Zero Trust Network Access (ZTNA) March 6, 2025/ Older Posts
Zero Trust Secure Access Services & ZTNA Solutions in Dubai, UAE

Articles Unlocking Modern Cybersecurity in the UAE, Middle East, and Dubai: A Deep Dive into IAM, PAM, and NAC Articles Unlocking Modern Cybersecurity in the UAE, Middle East, and Dubai: A Deep Dive into IAM, PAM, and NAC Articles February 25, 2025 In today’s rapidly evolving cyber landscape, traditional perimeter-based security is no longer sufficient to protect sensitive data and ensure secure remote access. Enterprises in Dubai, UAE, are increasingly adopting Zero Trust Secure Access Services and Zero Trust Network Access (ZTNA) Solutions to safeguard their digital assets. This modern security approach continuously verifies every user and device—regardless of their location—providing enhanced protection against sophisticated cyber threats. This article explores the Zero Trust Security Model, its key pillars, and how ZTNA solutions are transforming cybersecurity for businesses in Dubai and beyond. We’ll also delve into a real-world case study showcasing the successful implementation of ZTNA for the largest telecommunications company in the Middle East. Understanding the Zero Trust Security Model The Zero Trust Security Model is a comprehensive framework built on the principle of “never trust, always verify.” Unlike traditional IT models that assumed inherent trust for internal users, Zero Trust demands rigorous verification for every access request. This ensures that only authenticated users with compliant devices gain access to critical resources. Zero Trust is not a single product or protocol but a holistic approach to cybersecurity. It addresses the limitations of perimeter-based security by eliminating the concept of a “trusted” network zone. Instead, it treats every access attempt with equal scrutiny, minimizing risks such as lateral movement and unauthorized access. Key Pillars of Zero Trust Network Access (ZTNA) Implementing Zero Trust effectively requires attention to three foundational pillars: 1. Identity Every user’s identity must be verified—often using multi-factor authentication (MFA)—to confirm they are who they claim to be. This step ensures that only legitimate users can access the network. 2. Context The context of every access request is assessed, including factors like device type, location, and time. This ensures that access is both necessary and secure, reducing the risk of compromised credentials being exploited. 3. Security Posture The health and compliance of the device connecting to the network are continuously evaluated. This includes ensuring updated antivirus protection, system integrity, and adherence to security policies. The Role of the Trust Broker in ZTNA At the heart of ZTNA is the trust broker—a technology component that acts as an intermediary between the user and the application. The trust broker performs the following functions: Authenticates user identity. Checks contextual information. Monitors device posture. Once these checks are complete, the trust broker establishes a secure, per-application tunnel. This dynamic verification process minimizes risk by ensuring that only authorized access is granted for each individual session. From Perimeter-Based Security to Zero Trust Traditional network security relied on strong perimeter defenses like firewalls and routers. However, with the rise of cloud computing, mobile workforces, and remote access demands, these measures have become insufficient. Zero Trust eliminates the notion of a “trusted” network zone by treating every access attempt with equal scrutiny. This approach minimizes risks such as lateral movement—where an attacker moves from one compromised system to another—and significantly reduces potential damage. Case Study: ZTNA Implementation for the Largest Telco in the Middle East A comprehensive use case developed for the largest telecommunications company in the Middle East demonstrates the practical benefits of ZTNA in a demanding environment. Developed by SNSKIES, this document outlines how Zero Trust principles can be applied to enhance security, scalability, and remote access. Executive Summary In an era where remote work and digital connectivity are essential, the traditional VPN approach has proven architecturally limited. By implementing ZTNA, the telco addressed critical challenges such as: Unauthorized access Lateral movement Third-party vulnerabilities The solution leverages Fortinet’s advanced ZTNA capabilities to continuously verify user and device identities and enforce strict access controls—ensuring that only the necessary resources are accessible at any given time. Preventing Lateral Movement Traditional networks often allow attackers, once inside the perimeter, to move laterally and access multiple systems. In this case, ZTNA enforces micro-segmentation and the principle of least privilege access. Even if one system is compromised, the attacker cannot easily traverse the network, as access is tightly restricted to only the resources required for a specific user role. Minimizing Unauthorized Access The document highlights the importance of strict user authentication and continuous verification. By requiring multi-factor authentication and granular authorization for every application, ZTNA significantly minimizes the risk of unauthorized users gaining access to sensitive systems—even those already inside the network perimeter. Securing Vendor and Third-Party Access Another major focus of this use case is securing external access. ZTNA limits vendor and third-party connections by applying security tags and device posture assessments. This ensures that only devices meeting stringent security requirements can access designated network segments, thereby reducing the risk of external threats compromising internal resources. ZTNA Secure Access Gateway & ZTNA Over VPN The use case further distinguishes between two implementation models: 1. ZTNA Secure Access Gateway Utilizing Fortinet’s ZTNA access proxy (such as FortiGate), this solution proxies HTTP and TCP traffic over secure HTTPS connections. It authenticates users, verifies device posture, and sets up dynamic tunnels that enforce zero-trust policies for each session. 2. ZTNA Over VPN For organizations with existing VPN infrastructures, integrating ZTNA principles over VPN tunnels enhances security without a complete overhaul. By enforcing identity checks, contextual analysis, and posture verification over existing encrypted connections, this hybrid model provides a smoother transition to full zero trust while leveraging familiar tools. Summary The SNSKIES use case for the largest telco in the Middle East demonstrates a significant leap forward in secure remote access. By eliminating the traditional trust model and enforcing continuous verification and least-privilege access, ZTNA not only addresses critical security challenges such as lateral movement and unauthorized access but also enhances scalability and operational efficiency. Conclusion In an era marked by ever-evolving cyber threats, adopting Zero Trust Secure Access Services and ZTNA Solutions is essential—especially for enterprises operating in dynamic markets like Dubai,