Secure Your Business with SNSKIES Network Security Services!
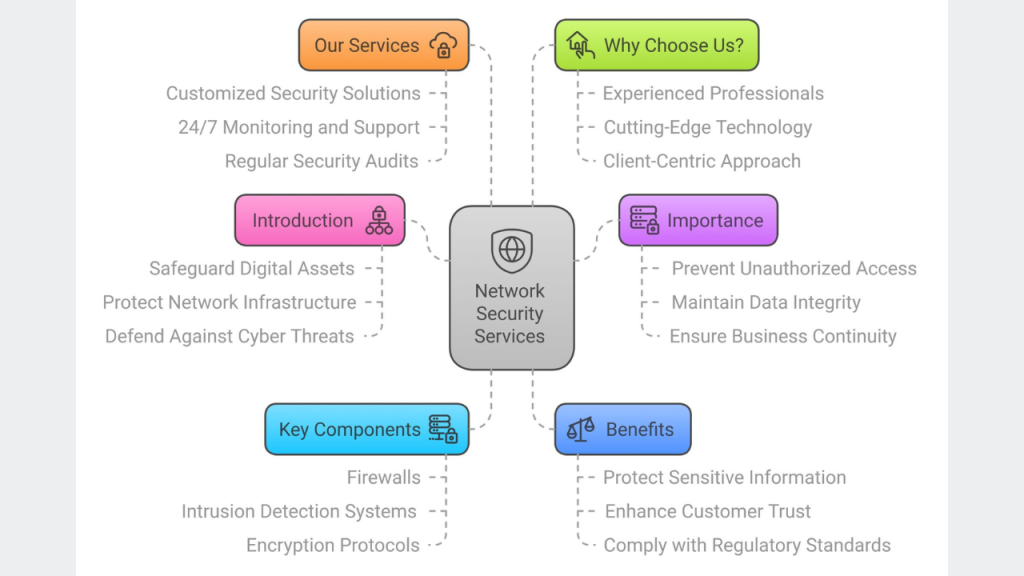
Secure Your Business with SNSKIES Network Security Services! Secure Your Business with SNSKIES Network Security Services! Blog January 2, 2025 At SNSKIES, we specialize in safeguarding your digital assets, ensuring data integrity, and defending against evolving cyber threats. From firewalls to advanced encryption protocols, our customized solutions are tailored to keep your business secure and compliant. ✨ 𝑾𝒉𝒚 𝑵𝒆𝒕𝒘𝒐𝒓𝒌 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑴𝒂𝒕𝒕𝒆𝒓𝒔:🚫 Prevent unauthorized access with advanced measures.📊 Maintain data accuracy and consistency.⚙️ Ensure business continuity with robust protocols. 🛠️ 𝑾𝒉𝒂𝒕 𝑺𝑵𝑺𝑲𝑰𝑬𝑺 𝑶𝒇𝒇𝒆𝒓𝒔:Customized security solutions for your unique needs.📡 24/7 monitoring to identify and address threats instantly.🔄 Regular security audits to stay ahead of vulnerabilities. 🏆 𝑾𝒉𝒚 𝑪𝒉𝒐𝒐𝒔𝒆 𝑺𝑵𝑺𝑲𝑰𝑬𝑺?With experienced professionals, cutting-edge technology, and a client-first approach, we ensure your business is secure, efficient, and resilient.
Enhancing Network Security in the UAE: A Comprehensive Guide by SNSKIES

Enhancing Network Security in the UAE: A Comprehensive Guide by SNSKIES Enhancing Network Security in the UAE: A Comprehensive Guide by SNSKIES Articles January 1, 2025 The Growing Importance of Network Security in the UAE In today’s digital age, businesses in the UAE are increasingly reliant on technology to drive growth and innovation. However, this dependence also exposes them to a wide range of cyber threats. From data breaches to ransomware attacks, the risks are real and can have devastating consequences. This is where network security plays a critical role in safeguarding sensitive information and ensuring business continuity. Why Network Security is Crucial for Businesses in the UAE The UAE is a global hub for commerce, finance, and technology, making it a prime target for cybercriminals. Here’s why network security is essential for businesses in the region: Protection Against Cyber Threats: With the rise of sophisticated cyberattacks, businesses need robust security measures to protect their networks. Compliance with Regulations: The UAE has stringent data protection laws, and businesses must comply with these regulations to avoid penalties. Safeguarding Reputation: A single security breach can damage a company’s reputation and erode customer trust. Ensuring Business Continuity: Network security helps prevent downtime and ensures that operations run smoothly. SNSKIES: Your Trusted Partner for Network Security Services At SNSKIES, we understand the unique challenges businesses in the UAE face when it comes to network security. Our network security services are designed to provide comprehensive protection against cyber threats, ensuring your business remains secure and resilient. Our Network Security Solutions Firewall Implementation: Protect your network from unauthorized access with advanced firewall solutions. Intrusion Detection and Prevention Systems (IDPS): Detect and block potential threats in real-time. VPN Services: Secure your remote connections and ensure data privacy. Regular Security Audits: Identify vulnerabilities and strengthen your network’s defenses. 24/7 Monitoring and Support: Our team of experts is always on hand to respond to any security incidents. Benefits of Choosing SNSKies for Network Security Tailored Solutions: We customize our services to meet the specific needs of your business. Cutting-Edge Technology: Stay ahead of cybercriminals with the latest security tools and technologies. Expert Team: Our certified professionals have extensive experience in managing network security. Proactive Approach: We focus on preventing threats before they can cause harm. Secure Your Business Today Don’t wait until it’s too late. Protect your business from cyber threats with SNSKies’ network security services. Visit network security services to learn more and schedule a consultation with our experts. Conclusion In a rapidly evolving digital landscape, network security is no longer optional—it’s a necessity. By partnering with SNSKies, you can ensure that your business in the UAE is equipped with the best defenses against cyber threats. Take the first step towards a secure future today. Ready to enhance your network security? Contact SNSKies now and discovern: Ready to enhance your network security? Contact SNSKies now and discover how our expert solutions can protect your business. Visit network security services
The Role of human Error in Cybersecurity Breaches
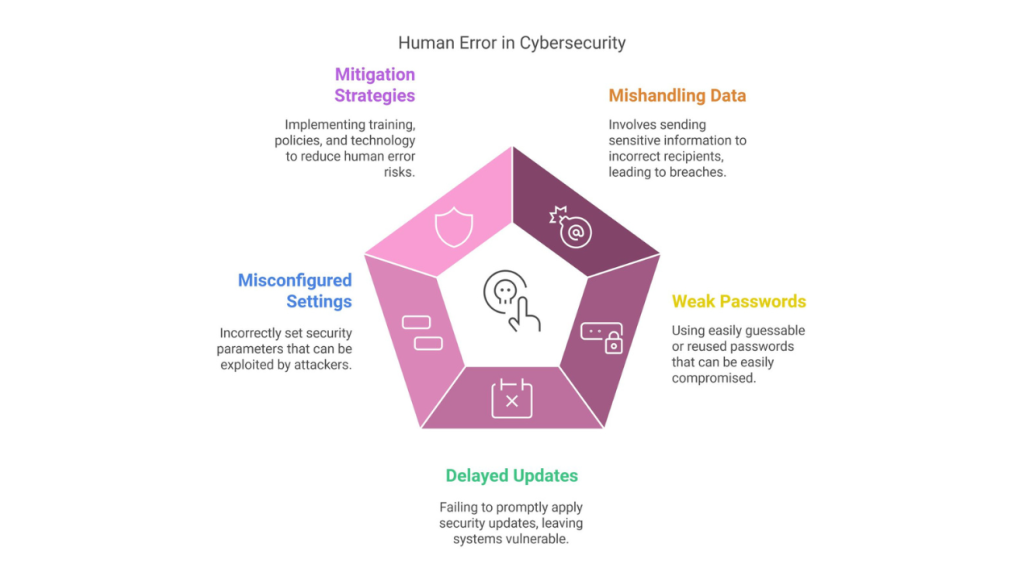
The Role of human Error in Cybersecurity Breaches The Role of human Error in Cybersecurity Breaches Blog December 11, 2024 Human Error: A Leading Cybersecurity Threat Did you know? Human error contributes to 73% of data breaches. Simple mistakes—like clicking phishing links or reusing weak passwords—create opportunities for cybercriminals to exploit vulnerabilities. The Real Impact of Human Error in Cybersecurity One striking case involved a $46.7 million loss in a Business Email Compromise (BEC) attack, where employees unknowingly transferred funds due to sophisticated phishing tactics. Top Causes of Human Error in Cybersecurity Mishandling sensitive data (e.g., sending it to unintended recipients). Weak or reused passwords that are easy to compromise. Neglecting software updates and security patches. Misconfiguring security settings, leaving systems vulnerable. Strategies to Minimize Cyber Risks Ongoing TrainingEducate employees about phishing, malware, and cybersecurity best practices. Enforce Strong Password PoliciesEncourage unique, complex passwords and require multi-factor authentication. Regular Security AuditsConduct phishing simulations and system vulnerability assessments. Leverage Advanced TechnologyImplement AI-powered threat detection, endpoint protection, and automated security tools. Building a Culture of Shared Responsibility Both organizations and individuals must take ownership of cybersecurity. Together, they can reduce errors and create a robust defense against cyber threats. Stay informed, stay secure. This optimized content emphasizes key points with SEO-friendly formatting, clear subheadings, and actionable takeaways to engage both search engines and readers.
Understanding Ransomware
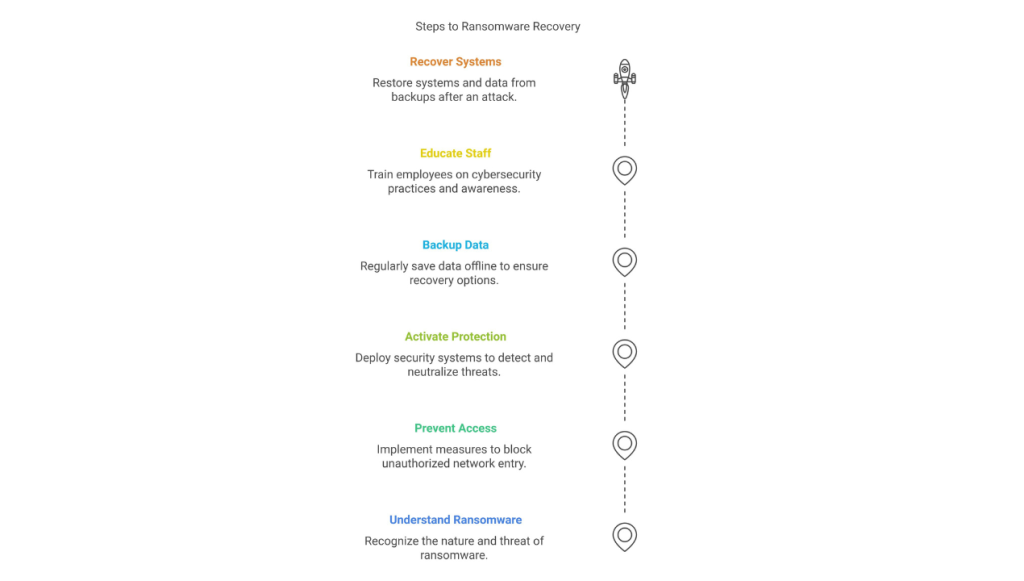
Understanding Ransomware Understanding Ransomware Blog December 10, 2024 𝐖𝐡𝐚𝐭 𝐢𝐬 𝐑𝐚𝐧𝐬𝐨𝐦𝐰𝐚𝐫𝐞?Ransomware is a type of malware that locks you out of your device or encrypts your data, demanding a ransom to restore access. 𝐇𝐨𝐰 𝐃𝐨𝐞𝐬 𝐈𝐭 𝐖𝐨𝐫𝐤? 𝐀𝐜𝐜𝐞𝐬𝐬: Hackers gain entry to your network and plant malicious encryption software. 𝐀𝐜𝐭𝐢𝐯𝐚𝐭𝐢𝐨𝐧: Devices are locked, and files are encrypted, rendering them inaccessible. 𝐑𝐚𝐧𝐬𝐨𝐦 𝐃𝐞𝐦𝐚𝐧𝐝: A message appears, demanding payment (usually in cryptocurrency) for decryption keys. 𝐒𝐡𝐨𝐮𝐥𝐝 𝐘𝐨𝐮 𝐏𝐚𝐲 𝐭𝐡𝐞 𝐑𝐚𝐧𝐬𝐨𝐦?Paying is not recommended as:There’s no guarantee of data recovery.Systems often remain infected.Paying incentivizes further attacks. 𝐇𝐨𝐰 𝐭𝐨 𝐒𝐭𝐚𝐲 𝐏𝐫𝐨𝐭𝐞𝐜𝐭𝐞𝐝:Keep recent offline backups of critical data.Implement robust monitoring and detection systems.Regularly update your software and train staff on cybersecurity best practices.
Protect yourself today with strong defenses, staff training, and regular system audits. Don’t wait for an attack to take action
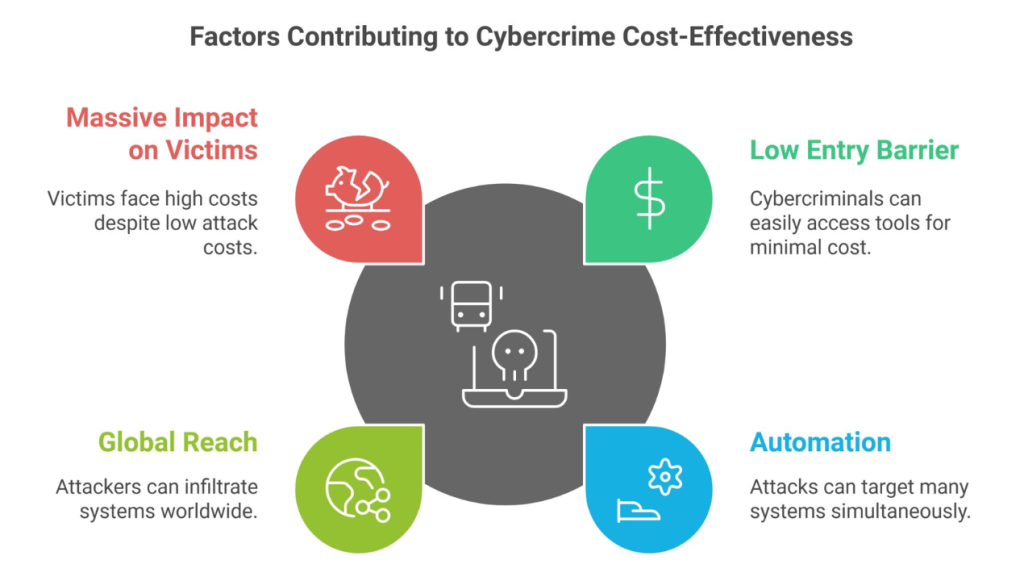
Protect yourself today with strong defenses, staff training, and regular system audits. Don’t wait for an attack to take action Protect yourself today with strong defenses, staff training, and regular system audits. Don’t wait for an attack to take action Blog December 9, 2024 🔧𝐋𝐨𝐰 𝐄𝐧𝐭𝐫𝐲 𝐁𝐚𝐫𝐫𝐢𝐞𝐫: Cybercriminals can purchase ransomware kits on the dark web for as little as $66. These kits include pre-packaged tools that require minimal technical expertise to use. 💻 𝐀𝐮𝐭𝐨𝐦𝐚𝐭𝐢𝐨𝐧: Many attacks are automated, allowing hackers to target thousands of systems simultaneously, maximizing damage at minimal cost. 🌐 𝐆𝐥𝐨𝐛𝐚𝐥 𝐑𝐞𝐚𝐜𝐡: With phishing emails and malicious links, attackers can infiltrate systems globally without significant additional effort. 💸 𝐌𝐚𝐬𝐬𝐢𝐯𝐞 𝐈𝐦𝐩𝐚𝐜𝐭: While the cost to execute an attack is low, the cost to victims is immense, often amounting to millions. Expenses include ransom payments, downtime, data recovery, reputational damage, and legal penalties. Don’t leave your organization exposed. Partner with SNSKIES to strengthen your defenses and safeguard your operations.
Introducing PROSE Technologies Modular Data Centers
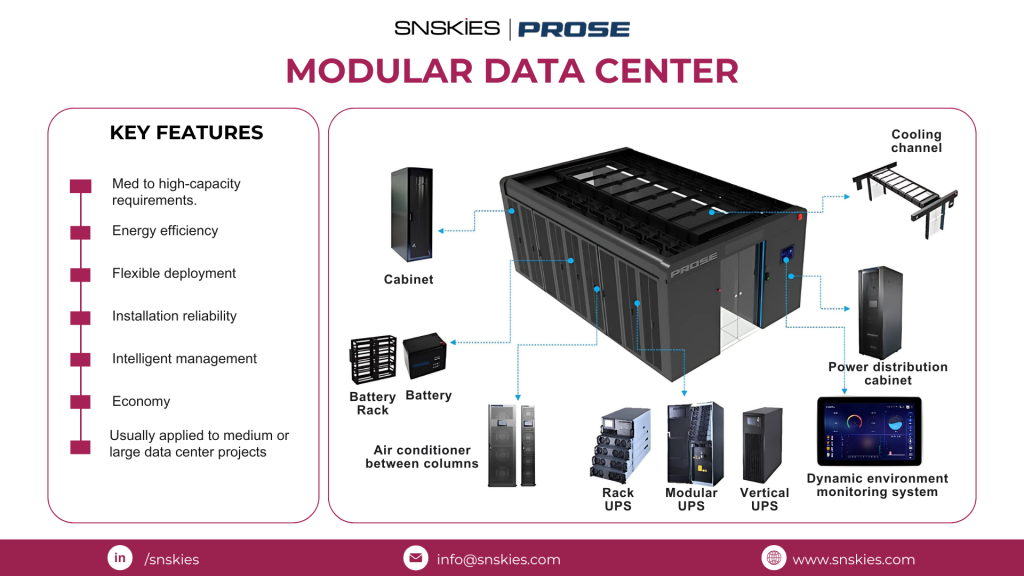
Introducing PROSE Technologies Modular Data Centers Introducing PROSE Technologies Modular Data Centers Blog September 30, 2024 Introducing PROSE Technologies Modular Data CentersReady for a data revolution? 𝗠𝗼𝗱𝘂𝗹𝗮𝗿 𝗗𝗮𝘁𝗮 𝗖𝗲𝗻𝘁𝗲𝗿𝘀 are the perfect solution for scalable and efficient data management. Prefabricated and flexible, they can meet your medium to high-capacity needs while ensuring energy efficiency and reliability. 𝗞𝗲𝘆 𝗙𝗲𝗮𝘁𝘂𝗿𝗲𝘀:Energy-efficient designFlexible deployment for any locationIntelligent management systemsCost-effective for large-scale projects 𝗨𝘀𝗲 𝗖𝗮𝘀𝗲𝘀:Edge Computing for reduced latencyDisaster Recovery solutionsRapid expansion for growing data needsIdeal for remote locations with limited infrastructureFuture-proof your data center now
Introducing the Electromagnetic Shielded Cabinet by SNSKIES | PROSE Technologies
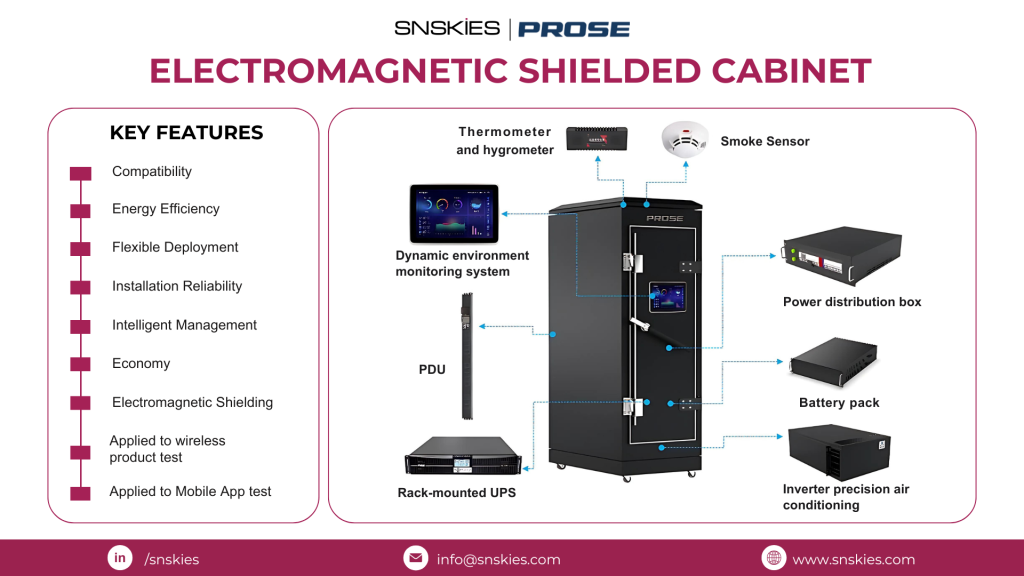
𝗜𝗻𝘁𝗿𝗼𝗱𝘂𝗰𝗶𝗻𝗴 𝘁𝗵𝗲 𝗘𝗹𝗲𝗰𝘁𝗿𝗼𝗺𝗮𝗴𝗻𝗲𝘁𝗶𝗰 𝗦𝗵𝗶𝗲𝗹𝗱𝗲𝗱 𝗖𝗮𝗯𝗶𝗻𝗲𝘁 𝗯𝘆 SNSKIES | PROSE Technologies 𝗜𝗻𝘁𝗿𝗼𝗱𝘂𝗰𝗶𝗻𝗴 𝘁𝗵𝗲 𝗘𝗹𝗲𝗰𝘁𝗿𝗼𝗺𝗮𝗴𝗻𝗲𝘁𝗶𝗰 𝗦𝗵𝗶𝗲𝗹𝗱𝗲𝗱 𝗖𝗮𝗯𝗶𝗻𝗲𝘁 𝗯𝘆 SNSKIES | PROSE Technologies Blog September 24, 2024 Our Electromagnetic Shielded Cabinet offers unmatched protection from electromagnetic interference (EMI), safeguarding sensitive electronic equipment in a variety of environments. With advanced features like energy efficiency, intelligent management, and reliable installation, it’s a vital solution for modern infrastructure. 𝗞𝗲𝘆 𝗙𝗲𝗮𝘁𝘂𝗿𝗲𝘀:Compatibility with various devicesEnergy Efficiency for optimized power consumptionFlexible Deployment optionsInstallation Reliability for peace of mindIntelligent Management system for real-time monitoringElectromagnetic Shielding for maximum protectionSuitable for Wireless Product & Mobile App Testing 𝗔𝗽𝗽𝗹𝗶𝗰𝗮𝘁𝗶𝗼𝗻𝘀:𝗗𝗮𝘁𝗮 𝗖𝗲𝗻𝘁𝗲𝗿𝘀: Safeguard IT systems from EMI and ensure reliable operations.𝗠𝗶𝗹𝗶𝘁𝗮𝗿𝘆 𝗮𝗻𝗱 𝗚𝗼𝘃𝗲𝗿𝗻𝗺𝗲𝗻𝘁 𝗙𝗮𝗰𝗶𝗹𝗶𝘁𝗶𝗲𝘀: Protect critical infrastructure from electromagnetic threats.𝗥𝗲𝘀𝗲𝗮𝗿𝗰𝗵 𝗟𝗮𝗯𝘀: Shield sensitive scientific instruments from external interference.𝗛𝗲𝗮𝗹𝘁𝗵𝗰𝗮𝗿𝗲 𝗙𝗮𝗰𝗶𝗹𝗶𝘁𝗶𝗲𝘀: Prevent interference with medical equipment, ensuring diagnostic accuracy. 𝗦𝗲𝗰𝘂𝗿𝗲 𝗬𝗼𝘂𝗿 𝗜𝗻𝗳𝗿𝗮𝘀𝘁𝗿𝘂𝗰𝘁𝘂𝗿𝗲 𝗧𝗼𝗱𝗮𝘆!Equip your facility with the ultimate protection and performance that the SNSKIES Electromagnetic Shielded Cabinet offers.
PROSE Technologies Outdoor Data Centers
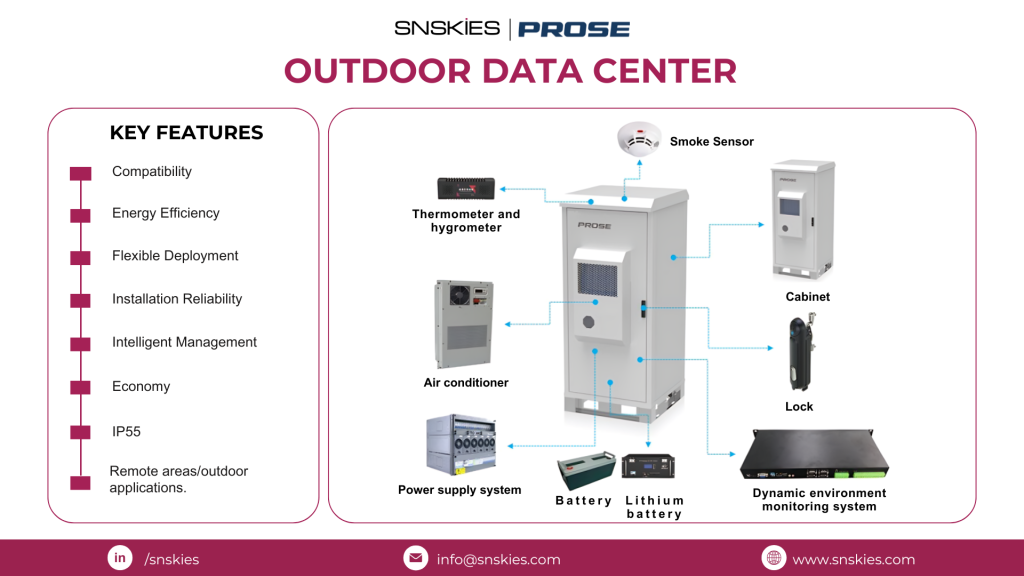
PROSE Technologies Outdoor Data Centers PROSE Technologies Outdoor Data Centers Blog September 24, 2024 Unlock the power of efficiency and flexibility with PROSE Technologies Outdoor Data Centers! 🌐💡 Built to withstand remote and outdoor environments, these solutions offer cutting-edge features like intelligent management, energy efficiency, and advanced cooling technology to ensure reliable operations in any condition. Whether it’s remote deployment or energy-saving optimization, our outdoor data centers redefine the future of IT infrastructure. Explore the future today!
PROSE KHIPU Micro Data Center
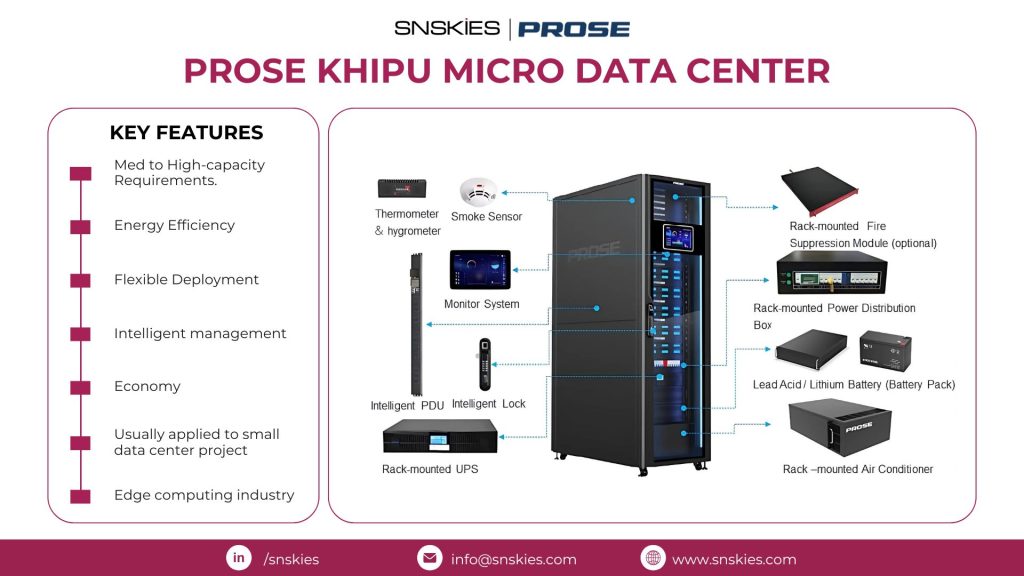
PROSE KHIPU Micro Data Center PROSE KHIPU Micro Data Center Blog September 20, 2024 We’re thrilled to announce our collaboration with PROSE Technologies to bring you the cutting-edge KHIPU Micro Data Center! Together, we’re set to redefine the digital landscape with innovative solutions tailored to meet medium to high-capacity requirements. Key Features: Energy Efficiency for sustainable operationsAdvanced Thermometer, Smoke Sensor & HygrometerOptional Rack Mounted Fire Suppression ModuleFlexible Deployment & Intelligent ManagementMonitor System & Intelligent PDUReliable Lead Acid/Lithium Battery optionsCompact Rack-mounted UPS & Air Conditioner Join us as we accelerate growth and drive innovation in the edge computing industry! Together, PROSE Technologies and SNSKIES are paving the way for the future!
Arshad Nadeem Makes History with Record-Breaking Gold at Paris 2024 Olympics

Arshad Nadeem Makes History with Record-Breaking Gold at Paris 2024 Olympics Arshad Nadeem Makes History with Record-Breaking Gold at Paris 2024 Olympics Blog August 10, 2024 In a stunning display of skill and determination, Pakistan’s Arshad Nadeem has made history by clinching the nation’s first-ever Olympic gold in athletics at the 2024 Paris Olympics. With a jaw-dropping javelin throw of 92.97 meters, Nadeem shattered the previous Olympic record of 90.57 meters, held by Norway’s Andreas Thorkildsen since 2008. Despite a shaky start with an initial failed attempt, Nadeem’s incredible second throw catapulted him to the top of the podium. He was the only one among the seven Pakistani athletes competing in Paris to receive backing from Pakistan’s National Sports Board for the Games. Reflecting on his groundbreaking achievement, Nadeem shared, “I’ve fine-tuned my technique, which made all the difference. This victory is just the beginning—I’m aiming to push beyond my 92.97-meter mark in the future.” Neeraj Chopra: A Fierce Competitor India’s defending Olympic champion, Neeraj Chopra, showcased his prowess by securing the silver medal with an impressive throw of 89.45 meters. He dominated the qualification round with a throw of 89.34 meters, surpassing Nadeem’s 86.59 meters. Yet, it was Nadeem who captured the spotlight as the only competitor to break the 90-meter barrier twice at the Paris Olympics, including a final throw of 91.79 meters. Chopra has been a formidable presence in international athletics, boasting a 9-1 head-to-head record against Nadeem. Their rivalry has captivated audiences, and fans eagerly anticipate their future encounters. Anderson Peterson’s Triumph Anderson Peterson of Grenada added to the excitement by securing the bronze medal with a stellar fourth-round throw of 88.54 meters, edging out Czech Republic’s Jakub Vadlejch. After claiming gold at the 2019 and 2022 World Championships, Peterson’s first Olympic medal in Paris marks him as the third Grenadian to achieve Olympic glory. A Thrilling Era in Athletics The spectacular performances by Nadeem, Chopra, and Peterson highlight the dynamic and competitive nature of global athletics. These athletes, hailing from nations traditionally underrepresented in the sport, have sparked intrigue and anticipation for their future showdowns. Stay tuned for more electrifying updates from the Paris 2024 Olympics and get exclusive insights into the world of athletics by subscribing to our newsletter. Witness history in the making as these athletes redefine the boundaries of excellence!