- Articles
Firewall vs. IDS vs. IPS: Understanding the Key Differences in Network Security
- Articles
Firewall vs. IDS vs. IPS: Understanding the Key Differences in Network Security
- Articles
- March 27, 2025
In today’s interconnected world, securing your network is no longer optional—it’s a necessity. Three common solutions that often come up in discussions of cybersecurity are firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS). Although they may sound similar, each plays a distinct role in protecting your network. In this article, we will explore the differences between these technologies, their key features, and how to choose the best option for your organization.
Table of Contents
- What Is a Firewall?
- What Is an Intrusion Detection System (IDS)?
- What Is an Intrusion Prevention System (IPS)?
- Key Differences Among Firewall, IDS, and IPS
- Benefits and Use Cases
- Choosing the Right Solution
- Conclusion
- Frequently Asked Questions (FAQs)
What Is a Firewall?
A firewall is often considered the first line of defense in network security. It monitors and controls incoming and outgoing network traffic based on predefined security rules. Firewalls can be hardware devices, software applications, or a combination of both.
Key Features of a Firewall
- Packet Filtering: Examines packets of data to allow or block them based on IP addresses, protocols, and ports.
- Stateful Inspection: Tracks the state of active connections to make filtering decisions more intelligent.
- Proxy Service: Acts as an intermediary for requests from clients seeking resources from other servers, adding an extra layer of protection.
- Application-Level Filtering: Analyzes data from specific applications (e.g., HTTP, FTP) to detect malicious activity.
What Is an Intrusion Detection System (IDS)?
An Intrusion Detection System (IDS) is designed to detect suspicious activities or policy violations within a network or host system. Unlike firewalls, IDS solutions typically do not block traffic; instead, they alert administrators about potential intrusions so that manual or automated responses can be initiated.
Types of IDS
- Network-Based IDS (NIDS): Monitors traffic across an entire network.
- Host-Based IDS (HIDS): Monitors traffic or system logs on a single host, analyzing user and system activities.
How IDS Works
- Signature-Based Detection: Uses known attack patterns (signatures) to identify threats.
- Anomaly-Based Detection: Establishes a baseline of normal activity and flags deviations as potential threats.
What Is an Intrusion Prevention System (IPS)?
An Intrusion Prevention System (IPS) takes the functionality of an IDS a step further by not only detecting malicious activities but also blocking or preventing them in real time. Think of it as an IDS with active response capabilities.
How IPS Works
- Real-Time Monitoring: Continuously scans network traffic for suspicious patterns.
- Automated Response: Blocks or quarantines malicious traffic based on predefined rules or anomaly detection.
- Integration with Other Security Tools: Often integrated with firewalls or security management systems to provide a coordinated defense.
Key Differences Among Firewall, IDS, and IPS
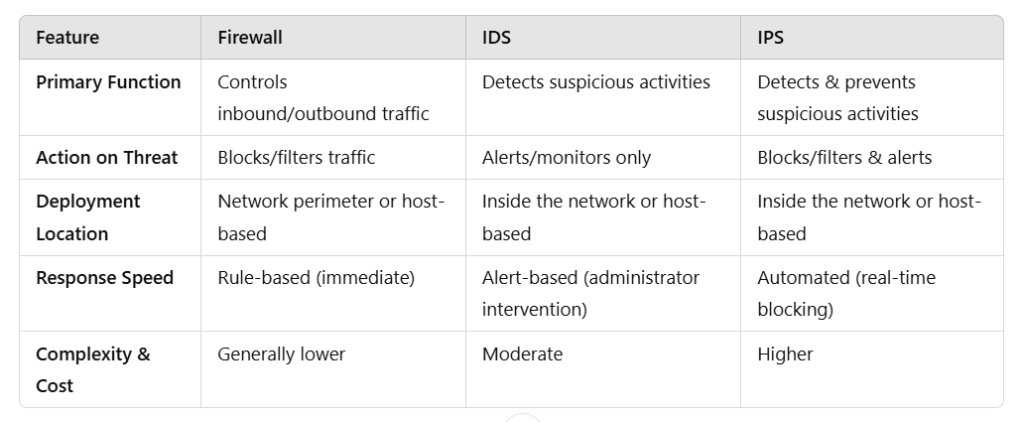
Benefits and Use Cases
Benefits of Firewalls
- Simple and Effective: Ideal for basic traffic filtering.
- Low Overhead: Generally less resource-intensive.
- Broad Coverage: Protects against a wide range of external threats.
Benefits of IDS
- Detailed Monitoring: Provides insights into network and system behavior.
- High Visibility: Offers comprehensive logs for forensic analysis.
- Adaptability: Can be configured to detect new or unknown threats using anomaly-based detection.
Benefits of IPS
- Proactive Security: Automatically stops attacks in real time.
- Reduced Manual Intervention: Frees up security teams by blocking threats automatically.
- Integrated Defense: Works well alongside other security tools for a layered security approach.
Choosing the Right Solution
- Assess Your Risk Level: Organizations with critical data and stringent compliance requirements may need an IPS for real-time blocking, while smaller businesses might start with a robust firewall and IDS combination.
- Consider Resources: An IPS typically requires more advanced configuration and monitoring. Ensure your team has the expertise to manage it.
- Layered Security Approach: No single solution is a silver bullet. A combination of firewall, IDS, and IPS often yields the best protection.
Conclusion
A robust security posture involves understanding the differences and synergies between firewalls, IDS, and IPS. While firewalls offer a foundational barrier, IDS provides deep visibility, and IPS delivers automated, proactive threat mitigation. Most organizations benefit from deploying all three in a layered security model to ensure comprehensive protection.
Frequently Asked Questions (FAQs)
No. Firewalls and IDS/IPS serve different but complementary roles. Firewalls block unauthorized traffic at the perimeter, whereas IDS/IPS focus on detecting and responding to threats inside the network.
Many modern security appliances combine IDS and IPS functionalities. However, in high-security environments, separate systems may be used for specialized monitoring and more granular control.
All are important in a layered security strategy. A firewall provides the first layer of defense, an IDS adds visibility and detection, and an IPS offers proactive prevention.
Not necessarily. An IPS offers automated blocking, but an IDS can be more cost-effective and simpler to manage, especially for smaller organizations or those with limited security expertise.
Look for reputable vendors with a proven track record, robust customer support, and solutions that can integrate with your existing infrastructure.
Recent Post
- All Posts
- Articles


